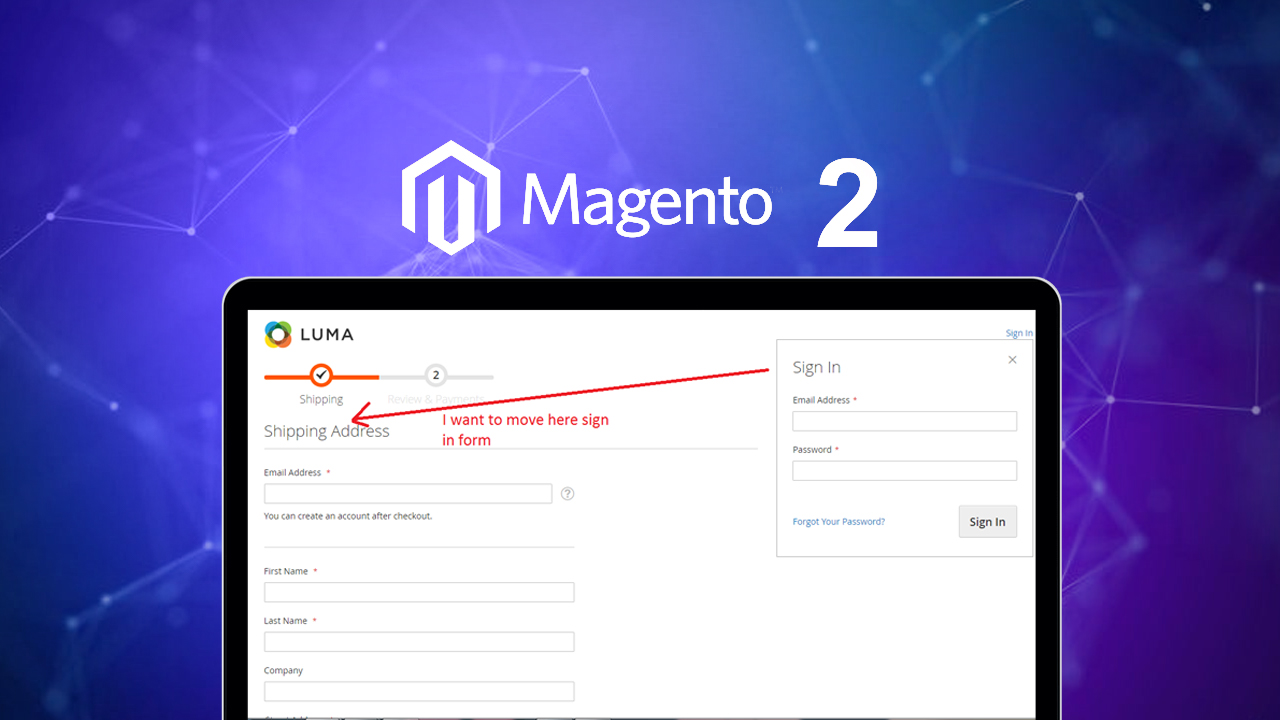
On October 08, 2024, Adobe released an important security update (APSB24-73) that influenced Magento Open Source, Adobe Commerce, and Adobe Commerce B2B platforms. This update addresses 22 security vulnerabilities, categorized as “Critical to Moderate”, making it essential for users to take immediate action.
Let us walk you through the October 2024 Adobe Commerce Security Patch Release notes.
ON THIS PAGE
Adobe Commerce Security Patch Release: Affected Products and Versions
Adobe Commerce on Cloud, Adobe Commerce on-premises, and Magento Open Source:
- 2.4.7-p3 and earlier
- 2.4.6-p8 and earlier
- 2.4.5-p10 and earlier
- 2.4.4-p11 and earlier
Critical Updates for B2B Users
This patch includes two critical updates for the Adobe Commerce B2B platform users. These vulnerabilities pose significant risks to the security of your online store and customer data. Ignoring them could lead to potential data breaches, loss of customer trust, and disruption of business operations.
Learn more About Adobe Updates
Why is this Update Important?
The timing of this release is particularly crucial with the holiday season approaching and ecommerce businesses are expected to see a surge in online traffic and transactions. Any security flaws during this period could result in severe financial and reputational damage. By applying this patch or updating to the latest magento version, businesses can safeguard their platform against cyber threats and ensure a smooth, secure shopping experience for their customers.
What if You’re Not Ready to Upgrade to the Latest Adobe Version?
For those who are not planning to upgrade to the latest version of Adobe Commerce or Magento Open Source, Adobe has provided a separate patch to address these vulnerabilities without a full upgrade. This patch can be applied independently to maintain security on specific files instead of complete system updates.
It is important to act immediately even if you choose the separate patch or upgrade the latest version. Cyber threats are constantly evolving, and delaying this security update can leave your store vulnerable to attacks.
View the full security bulletin provided by Adobe for more detailed information, including a breakdown of the vulnerabilities: Security Bulletin APSB24-73.
Don’t wait – secure your platform and protect your business now!
Key Takeaways:
- 22 vulnerabilities addressed, type is critical to moderate.
- 2 important updates specifically for Adobe Commerce B2B users.
- Apply the patch if a full upgrade isn’t possible yet this will modify only affected files.
- Secure your platform before the busy holiday season.
Stay proactive, stay secure, and ensure that your ecommerce platform is ready for the peak shopping season.
Solution for Adobe Commerce on Cloud, Adobe Commerce On-premises Software, and Magento Open Source
To help resolve the vulnerability for the affected products and versions, you should apply the CVE-2024-45115 Separate patch.
Separate Patch Details
Use the following attached Separate patch: Vuln-25610-composer-patch.zip.
How to Confirm the CVE-2024-45115 Patch is Applied in Adobe Commerce Cloud?
When dealing with security issues, particularly for Adobe Commerce Cloud, it is important to confirm whether separate patches have been successfully applied or not. This can be challenging, especially when there is no straight way to check if a specific issue, like CVE-2024-45115, has been patched. You can verify whether the patch was applied correctly by using the Adobe Quality Patches Tool.
Step-by-Step Guidance
Follow these steps to confirm if the CVE-2024-45115 patch is applied to your Adobe Commerce environment. In this example, we will reference the separate patch file VULN-27015-2.4.7_COMPOSER.patch.
1. Install the Adobe Quality Patches Tool
If you haven’t already, install the Adobe Quality Patches Tool to manage and verify patch applications. This tool simplifies the process of checking the patch status in your Adobe Commerce installation.
You can install it via Composer:
composer requires magento/quality-patches
2. Run the Patch Status Command
Once the tool is installed, run the following command to verify whether the CVE-2024-45115 separate patch has been applied. In this case, the command checks the status of the specific patch related to VULN-27015:
bin/magento-patches status
3. Check the Output
After running the command, see an output similar to the following, where the VULN-27015-2.4.7_COMPOSER.patch returns an “Applied” status:
Here, the patch with ID VULN-27015 shows the status as “Applied”, indicating that the separate patch for CVE-2024-45115 has been successfully applied.
4. Additional Notes
- Ensure that your environment is configured correctly to apply patches, and always test patches on dev and then staging environments before deploying them in production.
- If you face issues or the patch doesn’t show as applied, it may indicate a failure in the patching process, It’s requiring further troubleshooting and debugging.
Conclusion
By following the above steps, you can secure your Adobe Commerce environment and protect your online store from the potential risks posed by these vulnerabilities. Stay proactive and apply the latest patches to save your platform as the holiday season comes. Contact Klizer for any questions or expert consultation regarding the Adobe Commerce Security Patch Release.